Several days ago I was doing a routine Google search for a restaurant and I noticed something strange in the results: Some little icons — both to the left of the individual results, highlighting the destination brand (in this case, Yelp) — as well as underneath the blue link (here, the “EcoLink” icon and text). My first thought was that Google had added some new functionality and they’re testing it out on some suckers like me. However, I found the whole “EcoLink” thing a bit fishy sounding — kind of like somebody had hijacked those links and is providing some “valuable service” or “added benefit” to my clicking on those links.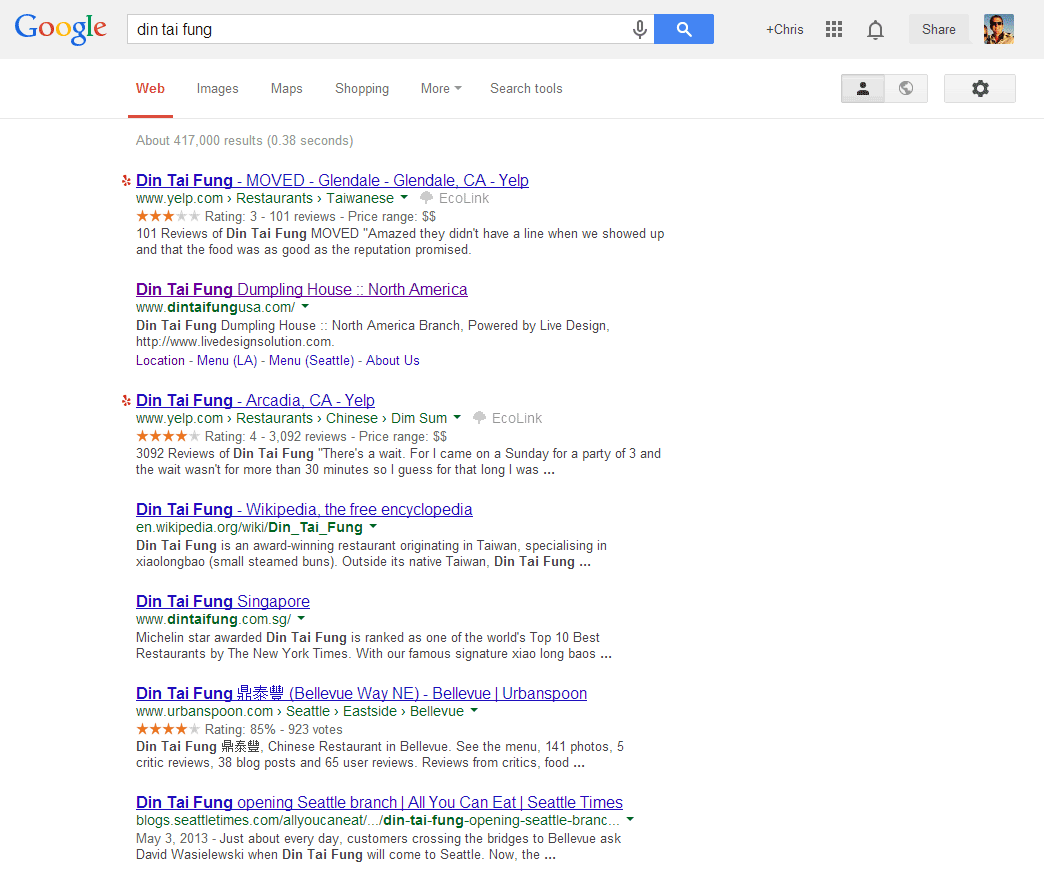
Upon further investigation and hovering over the “EcoLink” text, I noticed this copy in the tooltip: “This is an EcoLink and it helps the environment.” What? Clicking on this dim sum restaurant link to Yelp helps the environment? “If you buy something on this website after using this link, a percentage of your purchase will automatically be donated to a tree planting program in Brazil — at no extra cost to you!” Well I’ll be darned! If I actually purchase something on Yelp (is that even possible?) I’ll help plant a tree. How fantastic! But seriously, get out of my face, EcoLink.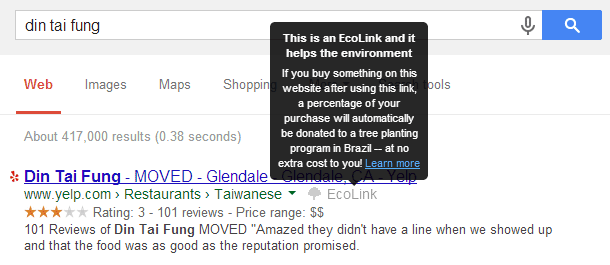
Had I had some inclination for planting trees in Brazil and specifically installed some extension or plugin to aid in my tree planting efforts, I may not be so bothered or perplexed, but I hadn’t. This showed up entirely without my knowledge. My next thought was, “alright, what extension or plugin did I inadvertently install or give permissions to that’s hijacking these links?” A quick review of my chrome extensions (chrome://extensions/ will do the trick) didn’t show anything of surprise. I went back to that Google results page and clicked the “Learn more” link and found this:
Seriously, Window Resizer (interesting, it now seems the extension has been removed from the Chrome Web Store)? A helpful tool for testing responsive web designs you absolutely are — but why risk losing your credibility with crap like this?
Furthermore, it actually does impact your browsing experience ever-so-slightly. By my estimation, quick math, and fuzzy debugging, my Google results page was slowed down by 499 milliseconds (about a half of a second); that’s not insignificant!
Goodbye, Window Resizer
Naturally, I dug into the extension settings and disabled EcoLinks. The author’s dark pattern enabled this by default, but I thought I could outsmart him.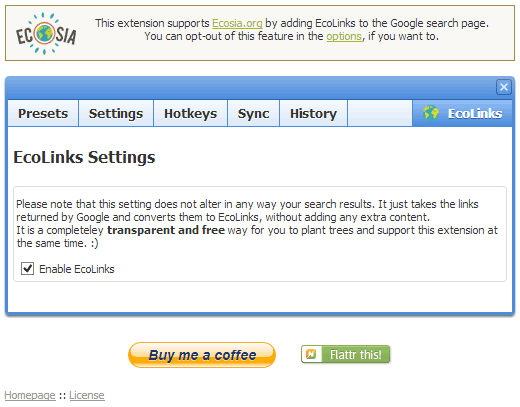
Sadly, I was terribly mistaken. It seemed that nearly every two-to-three days, the “feature” would automatically re-enable for some strange reason. My investigation was over, and as I thought more about it, I became increasingly weary of this particular Chrome extension, so I removed it entirely.
Extension Permissions
Now, I’m savvy enough to know that adding Chrome Extensions grants the extension permissions to certain things in your browser. There’s a risk we take by installing these helpful tools. I went back to check what permissions Window Resizer had requested of me, and I was pretty surprised with what I saw: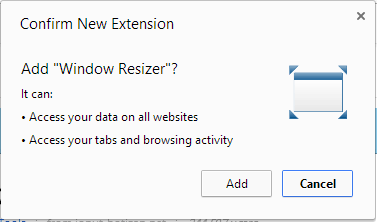
What I failed to realize is that I actually granted this extension with permissions to access my data on all websites. It’s actually a little more specific than that, and not necessarily as scary as it sounds, but still surprising. (Really, anything that runs JavaScript in your browser is a potentially dangerous weapon, but there’s just no way for Google Chrome to flawlessly know the intentions of these authors).
This reminded me of the significant risk we can face when installing such tools, helpful and great as they may be.
Beware, Browser Extension & Plugin Fans!
As seemingly innocent as the EcoLink link hijacking was from the Window Resizer plugin, I quickly realized something troubling…
I recently subscribed to LastPass, a fantastically-helpful tool to help remember and secure passwords to all of my online accounts. LastPass manifests itself in Chrome by installing a browser extension, much like Window Resizer. When I installed the LastPass Chrome extension, I granted it precisely the same permissions I granted Window Resizer: “Access your data on all websites” and “Access your tabs and browsing activity.” LastPass works by placing, via JavaScript, a handler on all of your web forms — and capturing what you’ve typed — to save the data (including usernames, passwords, and credit card numbers) for future re-use. It can even pre-populate — automatically — your usernames and passwords. Just think for a few moments how this could be used for malicious purposes by any old browser extension.
Surprisingly, even the author of the Window Resizer plugin seems to have acknowledged this fact in a recent changelog update:
Just think about it: I could have sold the extension to someone who would have gained access to all your passwords, emails, etc without you even knowing it. I haven’t done that!
Talk about losing credibility as a reputable developer! You may not have done what you “could have done,” but you did absolutely lose my trust. Whether planting trees or scraping my passwords, they’re both sneaky. I think the implied Hippocratic Oath of developers should include a promise to avoid trickery like this at all costs.
When a Chrome extension author publishes their extension, they must declare their intent in a manifest file. The permissions requested of users can be interpreted quite vaguely, and often extension authors are required to request permissions to do seemingly simple things that typically have no nefarious intent whatsoever. However, it’s entirely possible that a browser extension author could do a number of malicious things to compromise your privacy, identity, or sanity online.
Earlier this year, Lifehacker posted an interesting article, “Why Do Chrome Extensions Need to Access All My Data?” which explains some of the risks I’ve highlighted above. The most helpful piece of advice: Use common sense.
If an extension is asking for unreasonable permissions that don’t make any sense, you probably don’t want to install it.
Now might be a good time to go examine all of the browser extensions or plugins you have installed — and ditch those you haven’t used in a while, or suspect may be up to no good. Chrome users can navigate straight to chrome://extensions/ (wisely, Chrome won’t allow me to put a link to this URL here, but simply type it into your address bar to navigate) to investigate and review all of your extensions’ permissions.
Safe browsing, everyone!